In today’s digital landscape, security is a critical concern for organizations of all sizes. The rapid increase in data breaches, cyberattacks, and unauthorized access incidents has made it clear that traditional security methods are no longer sufficient to safeguard sensitive information. One of the most powerful tools in the arsenal of modern cybersecurity is Database Activity Monitoring (DAM).
Database Activity Monitoring (DAM) plays a vital role in protecting the heart of any organization’s data: its databases. Whether you are an enterprise with vast amounts of customer data, a financial institution with sensitive financial records, or a healthcare provider managing private patient information, ensuring the integrity and confidentiality of your databases is non-negotiable. This is where Database Activity Monitoring becomes a key component in enhancing security.
Database Activity Monitoring (DAM) is the #1 defense against these threats. This guide will show you:
✅ What Database Activity Monitoring is (and why it’s essential)
✅ How DAM works in real-time to stop breaches
✅ Top DAM tools compared (SentryOne, IBM Guardium, Oracle DAM)
✅ Use cases across industries (finance, healthcare, e-commerce)
✅ Implementation best practices
✅ Future trends (AI-powered monitoring, cloud-native DAM)
By the end, you’ll know exactly how DAM protects your data—and how to deploy it effectively.
Contents
What Is Database Activity Monitoring (DAM)?

1.1 Definition & Core Functions
Database Activity Monitoring (DAM) is a security technology that:
✔ Tracks all database interactions (queries, logins, changes)
✔ Detects suspicious activity (SQL injections, privilege abuse)
✔ Generates real-time alerts for threats
✔ Maintains audit logs for compliance (GDPR, HIPAA, PCI DSS)
1.2 How DAM Differs from Traditional Security
| Feature | DAM | Firewalls/IDS | SIEM |
|---|---|---|---|
| Focus | Database queries | Network traffic | Log aggregation |
| Threat Detection | SQL injections, data exfiltration | Port scans, DDoS | Correlates events |
| Compliance | Directly supports audits | Limited | Partial coverage |
Key Advantage: DAM provides deep visibility into who accesses what data—and how.
How DAM Enhances Security (6 Key Ways)
2.1 Prevents Insider Threats
- Detects unauthorized access (e.g., HR accessing financial data)
- Flags privilege escalation (admins abusing rights)
2.2 Stops SQL Injection Attacks
- Blocks malicious queries (e.g.,
' OR 1=1 --) - Example: A DAM tool stopped a credit card dump by alerting on abnormal
SELECT * FROM paymentsqueries.
2.3 Identifies Data Exfiltration
- Alerts on bulk exports (e.g.,
10,000+ rows downloaded) - Tracks suspicious connections (off-hours access from foreign IPs)
2.4 Ensures Compliance
- Automates audit logs for:
- GDPR (EU data access tracking)
- HIPAA (PHI access monitoring)
- PCI DSS (cardholder data protection)
2.5 Detects Database Misconfigurations
- Finds default passwords (e.g.,
sa/adminlogins) - Warns about weak encryption (unencrypted PII)
2.6 Provides Forensic Evidence
- Timeline reconstruction (Who changed what—and when?)
- Legal-ready reports for breach investigations
How DAM Works (Step-by-Step)
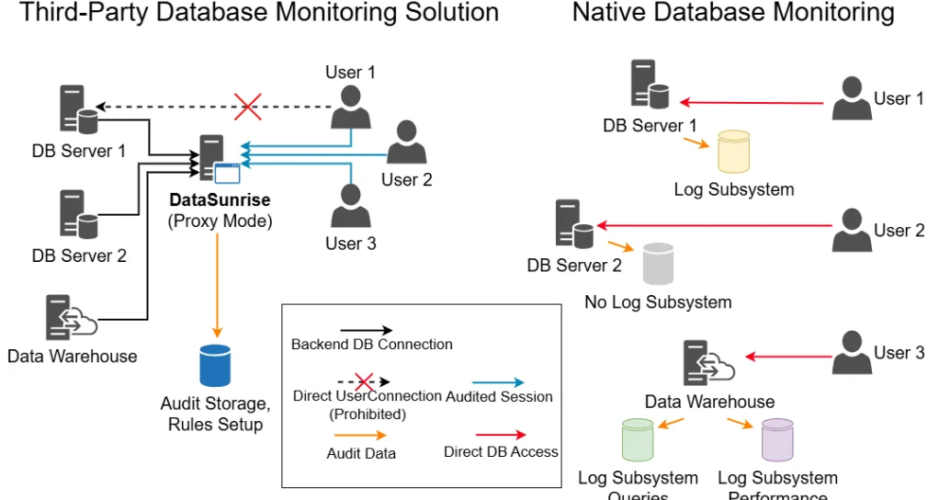
3.1 Data Collection Methods
- Agent-Based: Lightweight software on database servers
- Network-Based: Analyzes SQL traffic (no server install)
- Log-Based: Parses database audit logs
3.2 Real-Time Monitoring Flow
- Capture all SQL queries, logins, and schema changes
- Analyze for threats (ML models + rule-based policies)
- Alert security teams on risks (SMS, email, SIEM integration)
- Block malicious activity (via firewall or DB proxy)
3.3 Policy Examples
-- Alert on any SELECT from "credit_cards" table IF query LIKE '%SELECT * FROM credit_cards%' THEN trigger_alert(); -- Block midnight-to-5am access by non-admins IF user_role != 'admin' AND time BETWEEN 00:00 AND 05:00 THEN block_query();
Top DAM Tools Compared (2024)
| Tool | Best For | Key Feature | Price |
|---|---|---|---|
| IBM Guardium | Enterprises | AI anomaly detection | $$$$ |
| Imperva DAM | Cloud DBs | AWS/Azure/GCP support | $$$ |
| SentryOne | SQL Server | Performance + security | $$ |
| Oracle DAM | Oracle DBs | Native integration | $$$ |
Free Option: PostgreSQL Audit Extension (pgAudit) (Limited features)
DAM Implementation Checklist
5.1 Deployment Steps
- Inventory databases (SQL, NoSQL, cloud, on-prem)
- Define policies (compliance rules + threat patterns)
- Test in monitoring-only mode (avoid false blocks)
- Train staff on investigating alerts
5.2 Avoiding Common Mistakes
- Don’t monitor only production (test/dev need protection too)
- Do tune alerts to reduce noise (e.g., ignore backup jobs)
The Future of DAM (AI & Beyond)
- AI-Powered Anomaly Detection (Spot zero-day attacks)
- Cloud-Native DAM (Auto-discover DBs in AWS/Azure)
- Blockchain Auditing (Immutable activity logs)
Final Verdict: Is DAM Worth It?
✅ Yes if: You handle sensitive data (PII, payments, IP)
❌ No if: You only have public, non-critical databases
Next Steps:
- Start with a free trial (Imperva or SentryOne)
- Prioritize high-risk databases (Customer data first)
Database Activity Monitoring is a powerful tool in the fight against data breaches, insider threats, and cyberattacks. By providing real-time visibility into database activity, detecting suspicious behavior, and ensuring compliance with regulations, DAM plays a critical role in enhancing security.
Organizations that implement Database Activity Monitoring can better protect their sensitive data, maintain regulatory compliance, and respond to security incidents quickly and effectively. In today’s threat landscape, where cyberattacks are increasingly sophisticated, having a robust DAM solution in place is not just an option—it’s a necessity.